Porter
Overview
Porter can be described as the “Infura for TACo”. Porter is a web-based service that performs TACo-based protocol operations for applications.
Its goal is to simplify and abstract the complexities surrounding the TACo protocol to negate the need for applications to interact with it via a Python client. Porter introduces the TACo protocol to cross-platform functionality, including web and mobile applications.
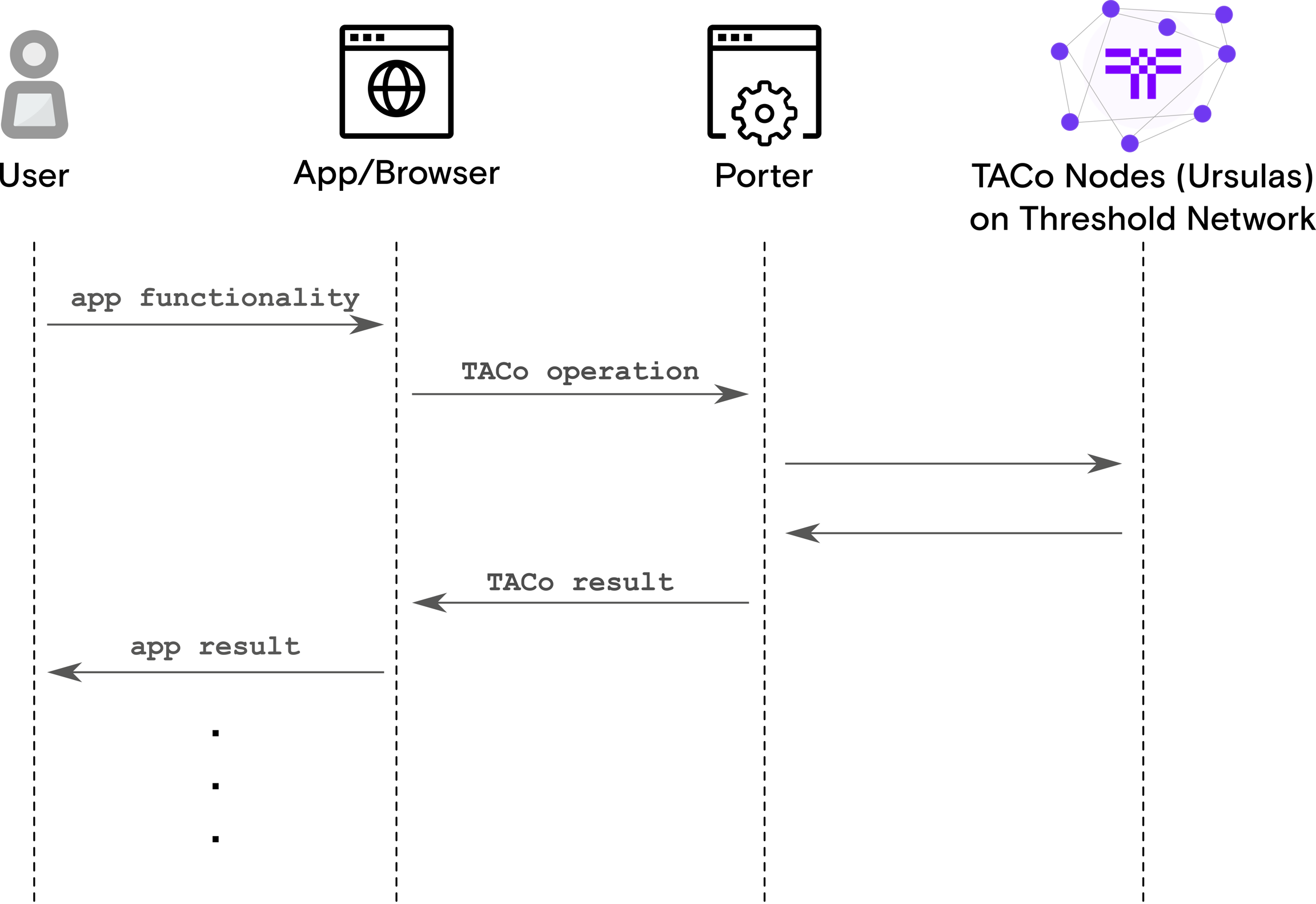
Any publicly available Porter instance can be used to interface with the TACo nodes, or some application developers opt to run their own.
Public Porter Instances
Public Porter instances are operated by centralized entities and have different security properties than user-operated instances.
To use the default Porter URIs in taco:
Alternatively, you can use your own non-default Porter URIs.
Last updated